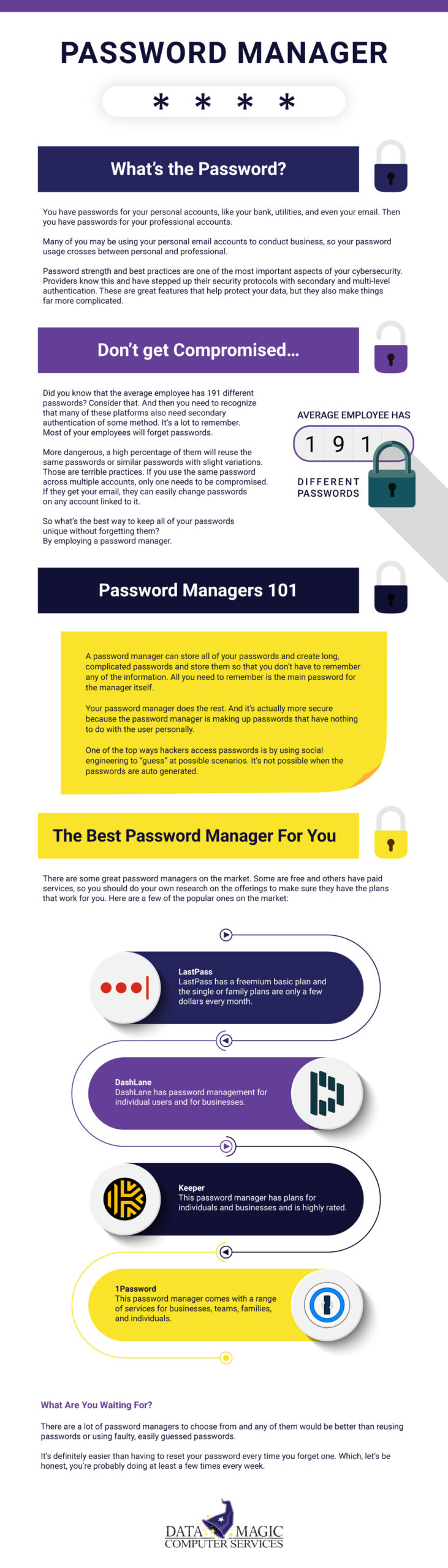
Can your company move away from an on-premise server to a SharePoint environment?
On-premise servers had their advantages in the past, but for most businesses, everything and more can be done in a Microsoft 365 SharePoint environment. This guide will help you identify whether you are ready to take the leap.
Table of Contents
- Applications:
- Computers:
- Internet Service:
- Microsoft 365 License:
- Files:
- Printing:
- Technology Partner:
- Other considerations:

Applications:
- Review all your applications – Are these currently web-based or hosted on your server?
- Adobe
- QuickBooks
- Business Specific Applications
- Office Products
2. If you are still hosting applications on your server, is there a cloud-based option?
- Review the cloud-based option to ensure the functionality is similar. If not, would the adjustment be easy? In most cases, the answer is yes.
Computers:
- Ensure your computers are less than 5 years old
- They must be equipped with an SSD as a hard disk drive can and will cause problems in a SharePoint environment
- Ensure their specs meet a minimum of: i5 processor, 256GB SSD, 16 GB of RAM
Internet Service:
Check on what type of connection you have
- Cable/Coax – if the first number (download speed) is larger than the second number, this is likely a coax connection. Example: 100/10
- Fiber – the download and upload speeds are identical. Example: 100/100
- Fiber is ideal for a cloud-based environment due to the higher upload dependency nowadays. However, a high enough cable connection would suffice depending on a few factors. Please reach out and we would be happy to audit this for you.
Microsoft 365 License:
Check what licenses you have. Most come with SharePoint and OneDrive. However, the Business Apps license does not.
Microsoft 365 Business Premium is highly recommended for a SharePoint environment for additional cybersecurity benefits. See our guide on Microsoft 365 Business Premium to see why this is the recommended license.
Files:
- Review the amount of data you currently have on your servers
- Review what data is live and would need to be migrated to SharePoint. SharePoint comes standard with 1TB but can be expanded if needed.
Printing:
In most cases, your printing is managed by the server. Ensure you have a solution for this to manage printing. Printix is a great option that we can implement for you.
Technology Partner:
- Evaluate your current IT provider. Do they have the expertise needed to set this up correctly? Microsoft 365 licenses are not cheap, having a provider that can maximize your subscription is critical.
- Ask your IT provider for references of similar projects they have completed.
- Contact us to get a FREE review of your systems to provide a SharePoint readiness report.
Other considerations:
- Multi-Factor Authentication should always be used with your Microsoft 365 license.
- Consider how you currently scan. Is it to a shared folder on a server? You may be able to scan directly into a SharePoint folder or you may want to switch to scan to email.
- All computers should be synced to OneDrive. There are many benefits to syncing your primary work computer to OneDrive. If your computer crashes, your files are still secure. As well as the ability to take your files with you wherever you go, among other benefits.