You have heard a lot about ransomware but do you know what it is and how to defend against it?
Cyber attacks have been happening at an increased rate all over the country. The most common type of cyber attack these days is ransomware. Ransomware is not a new form of hacking but it was not so successful in its early years. Now, cyber attackers have found ways to make it more profitable for them and that has lead to increased cyber attacks involving ransomware.

What is Ransomware?
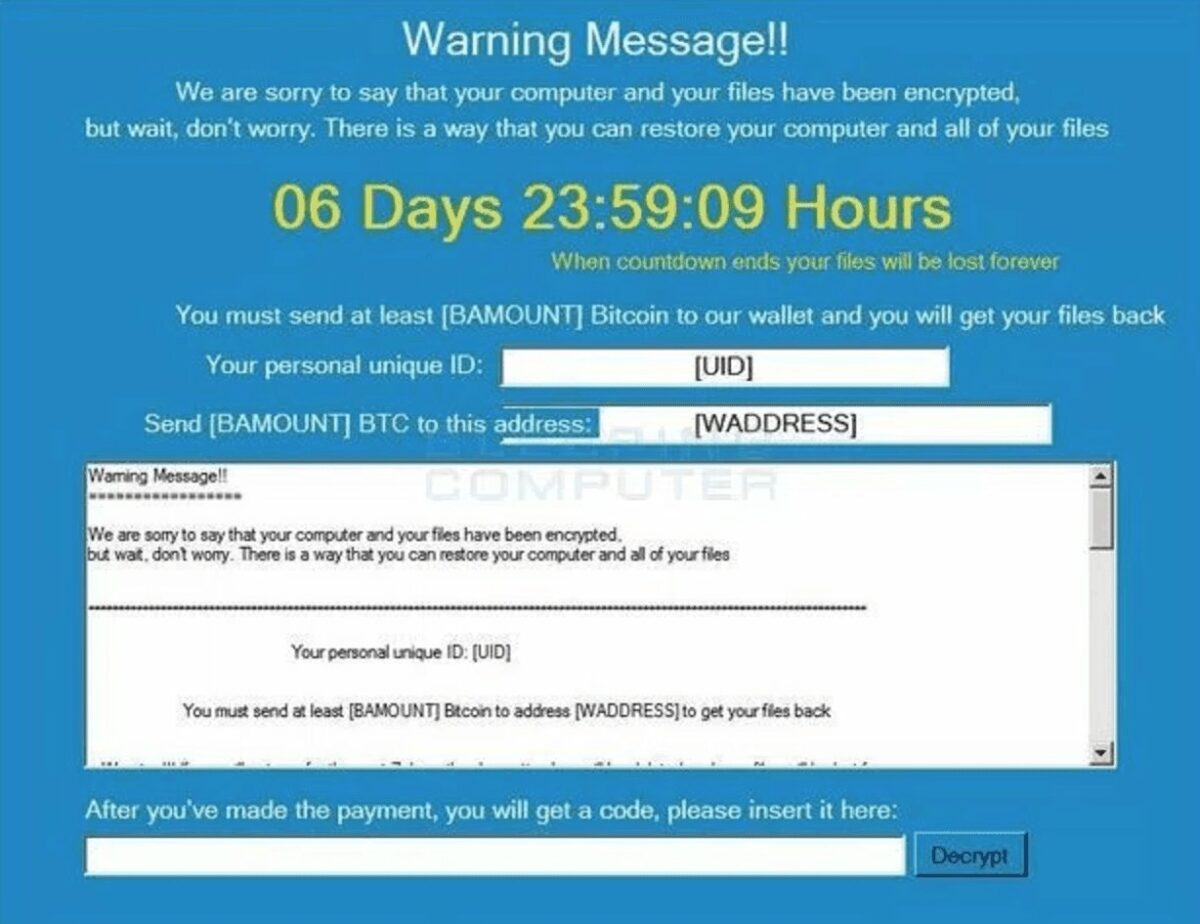
You may be wondering exactly what ransomware is. Ransomware is a type of cyber attack where cyber criminals gt into your system and take some of your files “hostage.” They likely will encrypt your data files so that you cannot gain access to them. In order for you to get your data files back, the hackers demand payment. In exchange for the payment, which is generally in bitcoins, a technology form of payment, you will be given an decryption key so that you can decrypt the data files and gain full access to them. This is generally how a ransomware attack plays out but there are different variations, including one called Popcorn Time when instead of paying the fee for the decryption key, you can provide the information of two other people or businesses for them to hack.
Where the Majority of Ransomware Attacks are Focused
While you may think that ransomware attacks happen to individuals more often than not, you would be incorrect. In fact, 88 percent of all ransomware attacks are focused on hospitals and healthcare organizations. More than any other sector or industry, hospitals and healthcare organizations lose the most data. On the black market, patient data sells for more money that anything else, which is likely the main reason why the industry is hit the hardest from cyber criminals. One reason why they may also be the most vulnerable is because hospitals use so many different systems and devices to get the work done. There are more entry and pivot points that cyber criminals can exploit and gain access to the system. 94 percent of the 88 percent of attacks were linked to a specific variant of software named Cryptowall. In fact, the hospital data breaches that have been high-profile enough for them to make headlines have been due to ransomware. This is becoming more and more of an epidemic, not only within the healthcare system but also in other sectors, even though they are not being hit as hard.
How to Protect Your Business
Whether or not your business is in the healthcare sector, you need to begin taking steps now to better protect your business against these types of attacks. They are occurring more and more often due to increased technology and experience in the hackers. This problem is not going to go away on its own and there needs to be a way for businesses to protect themselves. While it is impossible to eliminate the attackers at this point in time, there are ways you can better protect your business.
- Backup all of your files regularly. One of the biggest mistakes that companies make is not backing up their files. If you have a back up available, you will not have to pay the attackers to get your files back. You will already have them. Just be sure to keep them on a separate server and back them up regularly. The frequency of your backups will depend on how often your data changes. For some companies, it makes sense to back up once per week. For others, you will need to back up your files every hour. Figure out what works best for you and set it up accordingly.
- Install and maintain security software. Backing up your files should be done as a precaution. However, you need to have security software installed on all devices and keep them updated. This will help protect you against viruses and malware that you may be susceptible to.
- Educate yourself and your employees. Even with the best protection, hackers can still get in. Protect yourself and your company by taking the time to educate your employees on what to look for and what to do if they have noticed a virus or attack. The early reaction could be critical in slowing down or stopping the attacker.