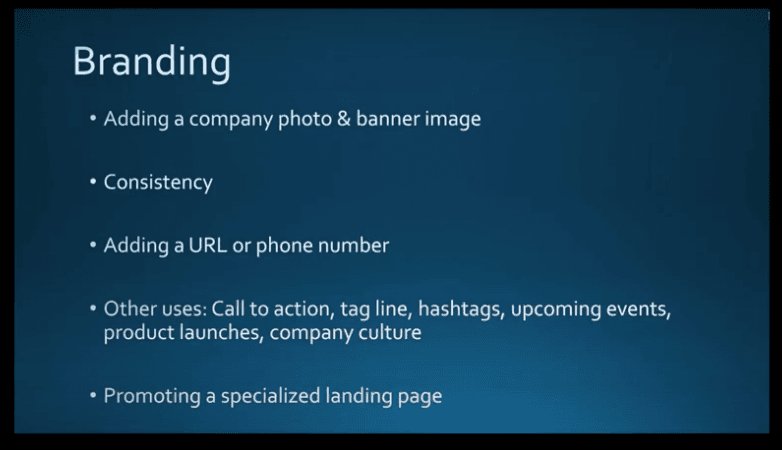
Cybercriminals are everywhere. Both domestically and around the world, countless hackers work day in and day out to penetrate the digital defenses of businesses just like yours, using a variety of proven, effective, and ever-evolving methods. Whether they infect your system with malware hidden in a seemingly innocuous email attachment or con an unsuspecting employee out of vital information through social engineering, the end results are the same: data loss, financial damages, lawsuits, reputational damage, bankruptcy, and worse.

Our team of certified system professionals understand how serious the modern threat of cybercrime is to businesses in your industry, which is why we’ve developed this whitepaper as a vital resource to show you how hackers think, what methods they use, and how you can stop them from victimizing your business. Without the right knowledge, tools, and technology to prevent hackers from stealing your information, your business is left prone to a major data breach.
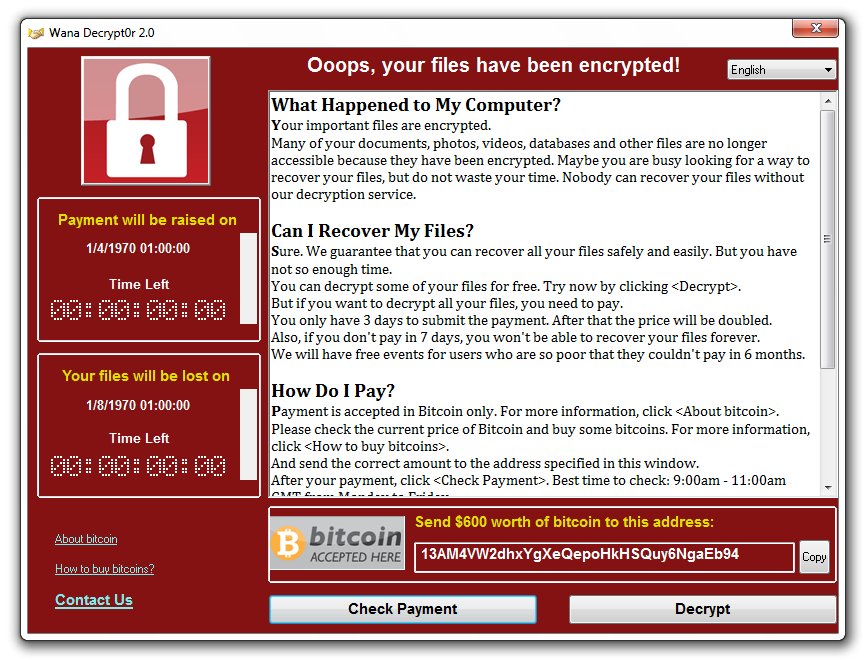
A recently popular type of malware is the “ransomware” variety, which encrypts a victim’s files (making them unreadable) and only offers the key to recover them after a ransom has been paid. The unfortunate reality is that when it comes to your business’ vulnerability to ransomware and other types of malware, it’s not a matter of IF, it’s a matter of WHEN. There are simply too many varieties of ransomware to guarantee total safety for your business.
IT security can be a complicated and scary subject when it comes to modern cybercrime tactics such as ransomware. Most business owners cannot confidently claim that their business’ network is secure. Can you?
When it comes to ransomware, the most important consideration is email security, and often, it can be as simple as ensuring that you and your staff know what to look for.
What makes a victim a victim?
The short answer is lack of awareness. Almost no hacking attempt can be a success without the victim playing at least some role in the process, such as:
- Visiting a malware-infected, unsecured website, either via an email, inappropriate browsing habits, or otherwise.
- Opening an untrustworthy attachment in an email from a hacker that’s disguised as coming from a sender such as a business contact, employee, client, government agency, etc.
- Downloading files that include a stow-away malware program or virus.
- Conducting any of the above while logged in with administrator rights provides even greater access to the hacker that’s infecting the system.
The bottom line is that digital security begins and ends with the user. Regardless of how modern, expensive or well-recommended your security software is, one wrong move by a single employee can be all it takes to infect your system. But that’s not the only threat to your security…
Is your technology making you an easy mark?
Outdated, unsecured, and just plain faulty technology is just as likely to make you an ideal target for hackers as an unsuspecting employee is. A major part of the investment in new technology is that it comes prepared to handle all previously identified hacking threats and security loopholes. The older your technology is, the more vulnerable it is to new hacking techniques.
Here are three vital considerations you should keep in mind when evaluating your current technology:
- Patch regularly, and patch often: Did you know that the most common way cybercriminals get into a network is through loopholes in popular third-party programs? That means the computer programs you rely on to get work done every day could be leaving you vulnerable to security breaches if you fall behind on updates. That’s why patch management is such a crucial part of proper IT security, in order to help you stay ahead of the non-stop tide of oncoming digital threats.
- End of Life (EOL) is FINAL: As good as it is to run a frugal business, it’s important to keep in mind that you’re not a college student trying to make an old, beaten up laptop last until you can afford a new one. You’re running a business, with much more to invest in and much more to lose. When your software reaches EOL, it will no longer receive the vital security patches it needs to keep you safe. At that point, as much as you may like the current operating system, you have to let it go and replace it with the new, secure version.
- Legacy technology isn’t worth the risk: Legacy software is often the gap in an otherwise capable suite of digital armor. Your business may have a brand new infrastructure, top-of-the-line security technology, and fresh-out-of-the-box desktops, but in the end, your unpatched, out of date legacy web browser will be what does you in. Just as with EOL, don’t let your favorite bit of technology put you at risk.
What is malware, exactly?
It’s a word you’ve probably heard a lot. You know it’s bad, and that you have software (anti-malware) designed to help you stop it. But in the end, if you don’t really understand how the enemy operates, how can you expect to defeat it?
Malware comes in many different forms and is used by hackers in a number of different ways. It can be used to steal information, locate vulnerabilities in your IT systems for a secondary attack, or simply to cause damage. While cybercriminals continue to innovate new forms of malware and the ways they use it, there are currently three main types that you should be familiar with:
- Malicious Scripts: This type attacks when you or a member of your staff visit the wrong web page. With the right conditions (user with admin rights, an outdated browser, lack of anti-malware software), simply loading the wrong web page is enough to infect your system.
- Embedded Media: While this form also attacks from a web page, it is through an infected media that is embedded in the site, such as a video or audio file. If your browser media player isn’t up to date (which is extremely common among today’s users), simply playing the media file can lead to a malware infection.
- Infected Files: The oldest form of the three is also the simplest. By downloading and running files (media codecs, screensavers, desktop images, etc.) that they haven’t properly inspected ahead of time, or that contain a hidden malicious file, the user openly invites malware into the system.
Types of Ransomware
While there are currently three basic forms of ransomware, cybercrime methodology is constantly evolving. In order to stay effective, hackers work non-stop to find new ways to deploy ransomware; keep in mind that best practices can quickly become outdated.
- Locker ransomware: This type works by denying access to the infected device. Generally, the scheme involves posing as a member of law enforcement and claiming that the victim has been a party to illegal activity (copyright infringement, illicit photography or media, etc.).
- CryptoLocker ransomware: This type employs powerful encryption to lock down the victim’s files and data, even if the malware is removed It usually makes its way to the user’s device through an email attachment that they are tricked into opening.
- Crypjoker: This form emerged as recently as January 2016, specifically targeting Windows operating systems to encrypt and lock down the user’s data. As opposed to CryptoLocker, Crypjoker gets to the victim as a PDF file attached to an email.
How Can You Keep Your Business Safe From Ransomware?
When developing your ransomware defense, keep these recommendations in mind:
- Make a considerable investment in a comprehensive backup data recovery solution so that you can restore your data at a moment’s notice when necessary.
- Test your backup and cybersecurity measures thoroughly and regularly; create dummy files and then delete them to see how fast they can be restored, or schedule a day to literally unplug your critical systems to find out how long it takes to get online again.
- Be sure to make the most of the available resources (both provided online and through expert IT consultants) to ensure that you’re not overlooking vulnerabilities in your IT security methodology.
- Employ email filtering, encryption, and continuity solutions to ensure that your lines of communication are secured.
- Equip your business with industry-tested security solutions like firewalls, antivirus, antimalware, and network monitors to keep your systems safe from external threats.
- Make sure your software and browsers are updated and patched on a regular basis.
- Train your employees in best practices for safe browsing and email conduct so that they don’t click the wrong link or download the wrong file.
Seems like a lot, right?
That can be a lot to handle for a business owner like yourself. You have clients to see to, employees to manage, and more on your plate every single day; should you really be expected to also oversee regular maintenance of your cybersecurity all on your own?
Of course not!
The best way to ensure that your business is kept safe is by outsourcing your cybersecurity management to a reliable and experienced Managed Services Provider like our Information Systems experts. For an easily budgeted monthly flat rate, you can enjoy the peace of mind that comes with knowing your business is safe from the whatever modern cybercriminals may throw at it.