Whether you’ve accepted it at your business or not, remote work is only going to grow and become a necessity for businesses to offer partial or full remote.
If you currently offer remote work or looking at potentially expanding this option, there are a few key items to consider.
Let’s lay out the most important remote work necessities.
Table of Contents
Hardware
User’s computers should be:
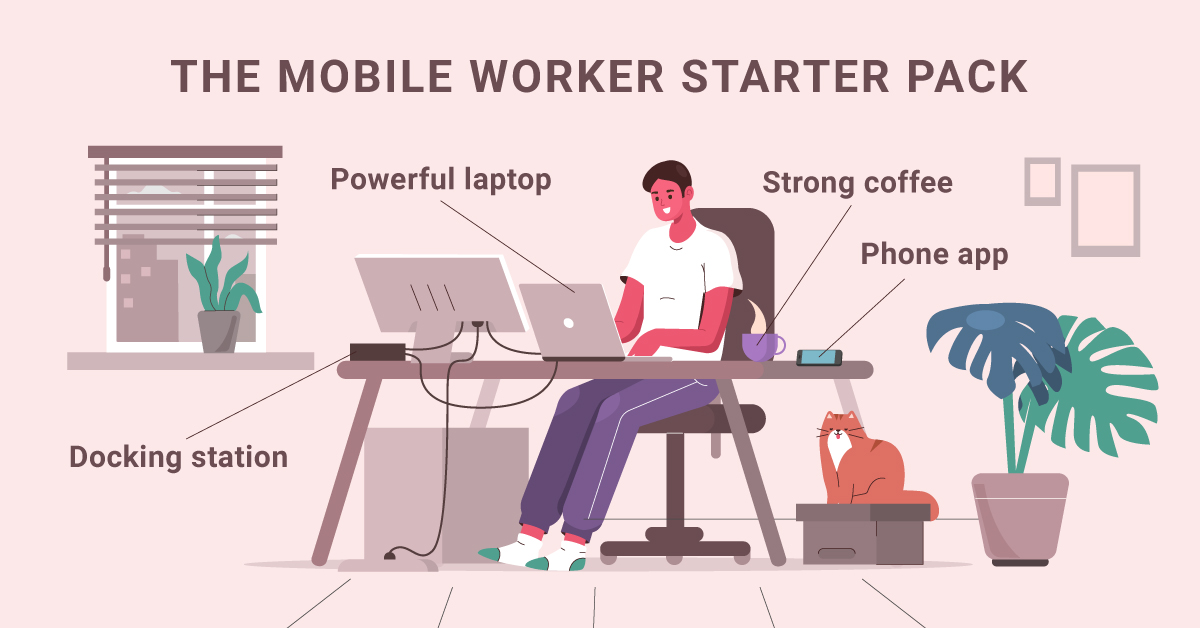
1. Laptop
or
2. Desktop at work AND home
Either of these computers are remote work necessities as they allow personal devices opens your organization to risk that can easily avoidable.
For desktop, it’s easy. Identical setup at your business and at their home
For laptop, here is the perfect setup:
1. Powerful laptop
2. USB Docking station - These are easier and more compatible than the old school “docking stations”
3. Dual Monitors – Now they have 3 monitors!
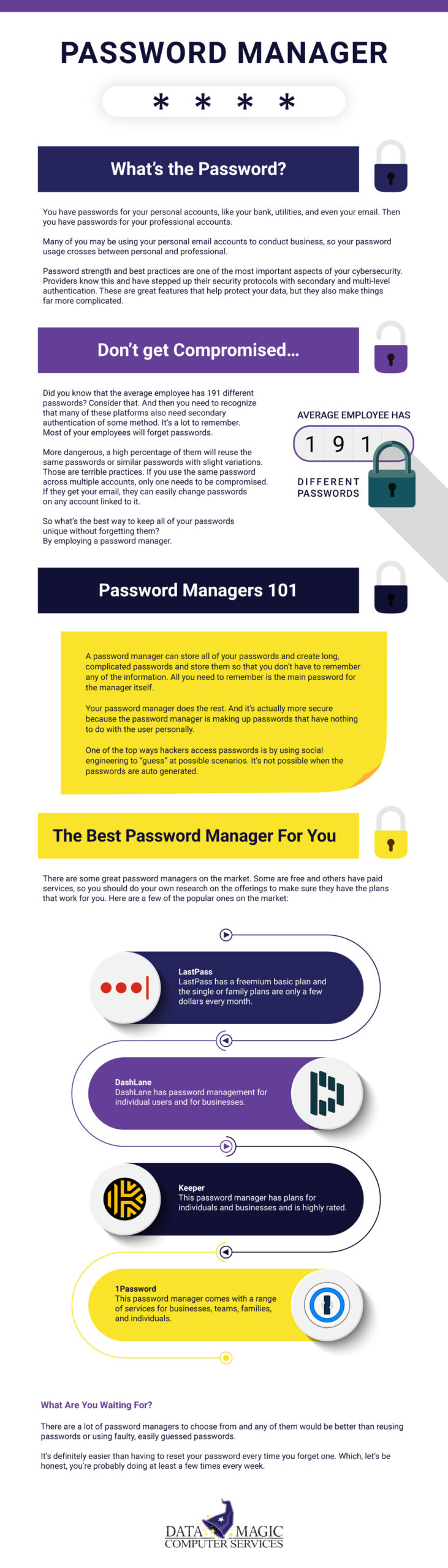
That’s it! Simple and easy. They unplug their laptop and connect the USB port and are instantly running at home.

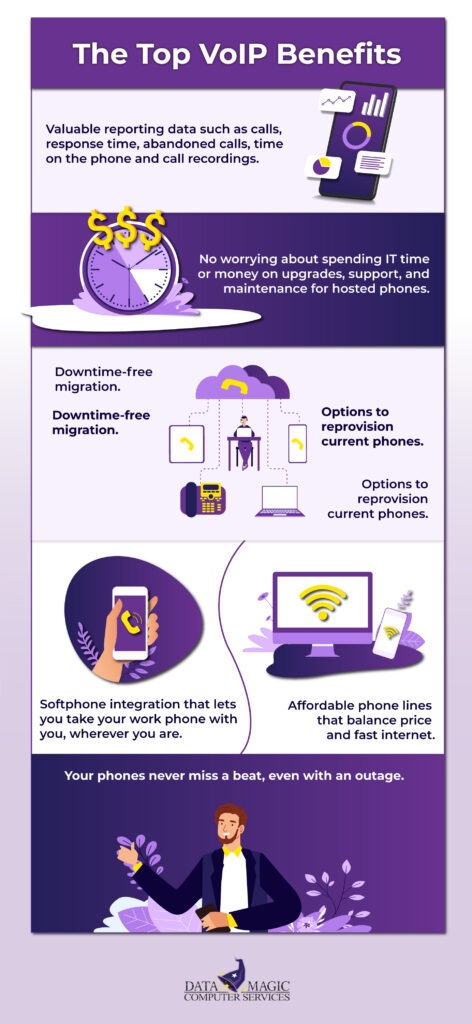
VoIP Phones: This is listed under hardware and are great remote work necessities, as physical phones are quickly becoming obsolete. Download the included software phone and provide an inexpensive headset for your employees and they easily take their work phone with them on their computer!
Access
There are lots of ways to make access easy without sacrificing security. Having your employees connect to the office to a physical server is the “old school” method that many businesses are still utilizing. Consider moving to SharePoint .
With SharePoint, folders can sync to the file explorer, so it looks just like what they’re used to! That data is then backed up, just like a server would be.

However, you may have business specific applications that is not cloud based and requires a server. These are becoming rarer but may still be applicable. I don’t want to get too technical, so you can reach out and we can provide an audit on the best solution for accessibility.
Moving to a hosted (cloud) solution or ensuring remote access for your users to your server onsite would be the primarily recommendations here.
Security
As mentioned, you don’t want users accessing company data on their personal devices. There are very easy force functions your IT provider can implement to ensure this is not occurring.
As more devices move away from the umbrella of the firewall (firewall is a physical device on your network that “filters” your internet data and protects computers at your business) you will need to ensure your security is focused on the computer and laptop, rather than the office location.
How do we improve the computer/laptop security?
There’s a lot that we do, and I’m sure your current provider may do too. Here is a quick summary of the highest benefit lowest impact layers you need to have in place:
- Multi-Factor Authentication – when the users log into their Microsoft accounts, they will be prompted with a push notification to their mobile device confirming it’s them This prevents 99% personal identify attacks… it’s a no brainer.
- Anti-Virus – There are lots of terms for this, but at the end of the day you need a trusted anti-virus on all computers.
- Conditional Access Policies – you want to make sure company data is NOT accessed on personal devices. Get your IT team to set this policy up and you’re all set. Need help? Let us know.
- Managed Detection and Response – This is the one all of those cybersecurity insurance questionnaires ask about. Make sure your provider has this on ALL machines.
There are more layers to consider for a remote work environment, but these are the non-negotiables.
Conclusion
Moving to an increased remote workforce should not be a scary proposition. If you embrace remote work necessities and make it easy for yourself and your employees, it will improve your business. Ensure employees have strong KPIs and that you have an IT team with ample experience in consulting and implementing these types of setups.