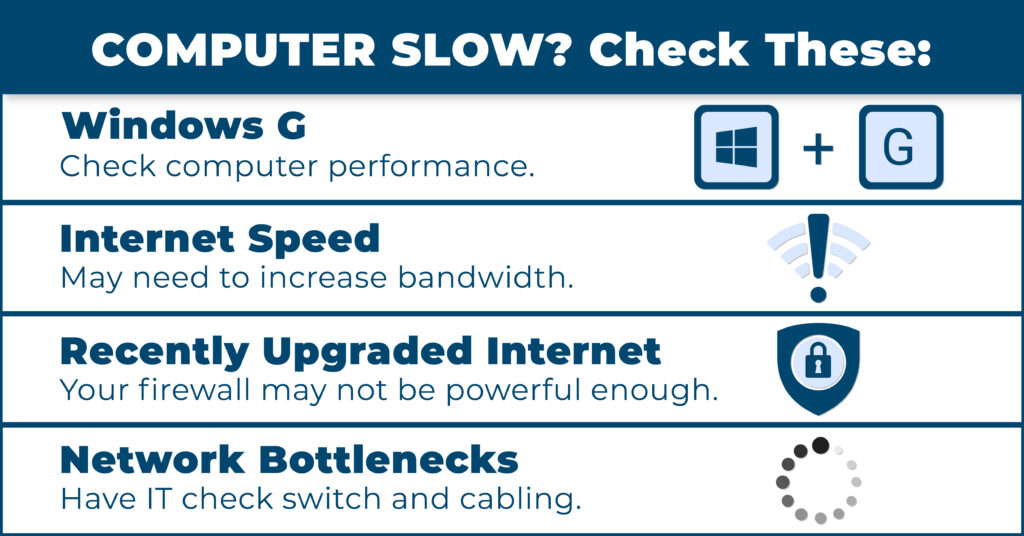
As a busy business owner, you’ve got plenty on your plate. Keeping your business efficient and on-target is crucial, but let’s face it: you don’t have time to dive deep into the technical details of every new software tool that comes along.
At Data Magic, we get it: you need your business’s IT operations to stay modern and competitive, but you have other things to spend your time on.
That’s why we’ve created a few non-technical guides to key tools or initiatives: our goal is to give you a quick read in plain language so you can make the right decision.
Today we’re covering Microsoft Intune: what it is, and what it can do for you.
What Is Microsoft Intune?
Microsoft Intune is a cloud-based endpoint management solution. But that’s not a very helpful term for nontechnical users, so let’s break it down.
- “Cloud-based” means it runs in the cloud, rather than on your servers.
- “Endpoint management” is the process of setting up user access, determining who can do what with their company devices, and keeping user devices up to date without having to manually install every single Windows update.
Essentially, Microsoft Intune is a solution that helps your business control two things:
- User access: who can see, download, and edit which files, documents, and so forth
- The devices those users use: what software is preloaded, what can they install on their own, security updates, and so forth
It’s a part of the Microsoft 365 (formerly Office) suite that you’re likely already paying for, and it’s an incredibly powerful tool. That said, it’s not as end-user- or beginner-friendly as Word or PowerPoint or Outlook.
Setting up and using Intune can seem like a lot. But the benefits are worth the investment. And if you need a partner to help you move forward, we should chat!
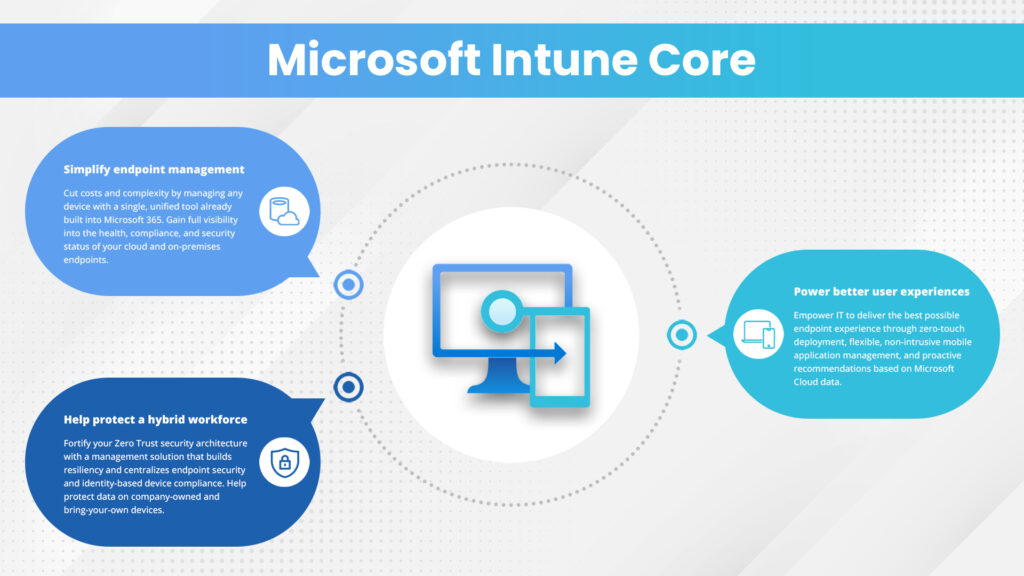
Top Benefits of Microsoft Intune for Your Business
Here are the top benefits of Microsoft Intune for your business — explained in terms that don’t require a computer science degree.
1. Simplifies the process of equipping employees with new computers
When you hire a new employee or give a current one a newer computer, someone has to set it up. Someone has to connect the cables and plug the thing in, but you also have to worry about software.
Most businesses have moved past manually installing Office, Slack, Salesforce, and whatever other desktop apps a user may need. It’s time-consuming to do this and imagine if you hired 10 new employees (or 100!). Manual installs aren’t scalable.
So instead, businesses use one of several methods to automate parts of this process.
This may be called imaging or provisioning a device. It can happen on-site, where a tech essentially copies an existing device setup (an image) onto the new device’s hard drive.
But it can also happen via the cloud, thanks to Microsoft Intune.
In our remote-focused world, this is a big deal. With Intune, you can ship a computer to a new employee. All they need is a login, and Intune pushes all the software and settings they’ll need onto their device — automatically.
2. Automate your IT policies and security settings
Even after every employee has a functioning PC with the right software installed, there’s no accounting for the sorts of things those employees will try to do with their machines. Just like Intune can push the right software and software updates to a device automatically, it can also impose the IT policies and cybersecurity “guardrails” that your business sets up. (Your IT partner can help with figuring out what these should be.)
This way you’re not constantly putting out fires, telling people to stop doing x or y and trusting they’ll do it, or just hoping for the best that the policies you initially set up won’t get changed or go out of date.
With Microsoft Intune, all of this can be managed remotely. Need to change a security setting due to a new threat? Change it in Intune, and the change gets pushed to every user’s PC.
3. Integrates with the rest of Microsoft 365 (and other Microsoft services)
More than likely if you’re looking into Intune you’re already using other Microsoft products: your workforce is using PCs running Windows, and you’re probably already paying for them to have access to Microsoft 365 (the productivity suite containing Word, PowerPoint, Excel, Teams, Outlook, and something like 50 additional tools).
If that’s true, then it means Intune could be effectively free for you depending on the subscription you have. But even more importantly, it means that Intune integrates closely with all those other Microsoft products and services you’re using. (Integrations aren’t rare and aren’t exclusive, but when you stick with products made by the same company you tend to get better, more robust integrations.)
When used to the fullest, these integrations give you a comprehensive approach to security, analytics, deployment, and endpoint management. For many businesses, doing it this way is far less hassle than using dedicated solutions from various providers for each of these functions.
4. Works with mobile threat defense services
Endpoint management deals with the devices your company owns. But what do you do about employees who want (or even need) to access company resources from their phones or laptops?
Most companies offer a correlating service for mobile threat defense, and Microsoft is no exception. Microsoft Defender for Endpoint is the first-party option, and there are plenty of others out there.
With these services, you’ll be able to control what mobile devices can access and keep your company’s IT resources safer. And if you choose Defender for Endpoint along with Intune, you’ll get a harmonized, integrated experience.
5. Enables access control and conditional access
This one can get technical in a hurry, but we’ll keep it straightforward: not everyone in your business should have access to everything in your IT environment. Deciding and enforcing who can see/edit/download/delete what is called “access control”.
Conditional access works alongside, setting other sorts of limits to access. You might block all access from certain regions (where you have no employees) to keep out cybercriminals who snagged a stolen login. You might block access at certain hours, too: if no one would ever need to access files at 2 am and someone is doing so, that someone is very likely up to no good.
Intune makes both access control and conditional access simple enough for businesses of just about any size to implement.
These are just five of the many benefits your business could experience by leveraging Microsoft Intune. Got questions? Not sure about an internal deployment? Data Magic has your back. Give us a call or send us a message today!