The Newest Forms Of Ransomware & How To Protect Your Business From Them
The Situation
Ransomware is now one of the top security concerns for businesses and organizations of all sizes. The City of Atlanta was hit with a ransomware attack called SamSam in March, crippling some important departments like their court system, sewer infrastructure requests, and water billing department.
The attackers who deploy SamSam are known for clever, high-yield approaches. This, combined with the City’s lack of preparedness, explains why the infection was so debilitating.
Experts are telling us that SamSam will strike again. Unlike many forms of ransomware that spread via phishing attacks where individuals inadvertently invite the attack, SamSam exploits IT system vulnerabilities and cracks weak passwords. These ransomware attackers have made $1 million in less than six months.
Keeping all your systems patched, storing data in enterprise-based cloud backups, and having a ransomware preparedness plan can offer real protections against SamSam and other ransomware infections.
Unfortunately, ransomware attacks are on the rise, and as hackers use more sophisticated encryption technology, the threat is constantly evolving. According to malware security firm Barkly, a company is hit with a ransomware attack every 40 seconds. They also identified ransomware as the most prevalent form of malware, with “4.3x new ransomware variants in Q1 2017 than in Q1 2016.”
This eBook details how dangerous ransomware is, how it could harm your business, and what you should do to protect your data.
Part 1
What is Ransomware?
Ransomware is a type of malicious software (malware) that blocks access to a computer that infects, locks or takes control of a system and demands a ransom to unlock it. It’s also referred to as a crypto-virus, crypto-Trojan or crypto-worm. It then threatens that your data will be gone forever if you don’t pay using a form of anonymous online currency such as Bitcoin.
Most forms of ransomware are spread via spam using unsolicited phishing email or an attachment. Phishing attacks use emails disguised to look like they’re from someone you know and are more likely to trust.
Some ransomware-based applications disguise themselves as police or a government agency, claiming that your system is being locked down for security reasons and that a fine or fee is required to reactivate it. Then it typically asks you to click on a link or attachment to perform a routine task such as updating records or account details. If you do this, a worm or malware is downloaded, infects your system and locks it by encrypting your files.
Ransomware, like SamSam, can also infect your IT system using vulnerabilities in your computer’s browser. It does this when you click on a malicious code hidden in online ads or free software.
Ransomware targets small to medium-sized businesses because they are particularly vulnerable due to limited IT resources. They are also more likely to pay the ransom in the hopes that they’ll get access to their data, although the FBI warns that this isn’t necessarily so.
“Paying a ransom doesn’t guarantee an organization that it will get its data back—we’ve seen cases where organizations never got a decryption key after having paid the ransom. Paying a ransom not only emboldens current cybercriminals to target more organizations, but it also offers an incentive for other criminals to get involved in this type of illegal activity. And finally, by paying a ransom, an organization might inadvertently be funding other illicit activity associated with criminals.”
Paying the ransom only guarantees that the malicious actors receive your money, and possibly even banking information. Also, decrypting files does not mean the malware infection itself has been removed.
No one is immune.
- Temporary or permanent loss of sensitive or proprietary information,
- Disruption to regular operations,
- Financial losses to restore systems and files, and
- Potential harm to your organization’s reputation.
The lack of awareness and cybersecurity training is a leading cause of ransomware.
Part 2
Ransomware Comes in Many Forms.
Ransomware comes in many different forms, but essentially, it’s a type of malware that denies access to your computer devices unless you pay a ransom. The ransomware malware encrypts your data. Once it does this, it can travel throughout your network and encrypt other mapped and unmapped network drives. Because of this, it can bring your organization to a halt.
The ever-evolving nature of these threats makes ransomware very difficult to keep track of. Ransomware-as-a-Service (RaaS) makes it easy for cybercriminals to set up a lucrative hacking scheme. It is provided as a vendor platform on the Dark Web. Unlawful vendors offer hackers and criminals a tool to use to lock down computer files, information or systems and hold them hostage.
Ransom32 is a type of “Ransomware-as-a-Service” that provides any cybercriminal, even those without technical knowledge, the ability to create their own form of ransomware. What makes Ransom32 so dangerous is that it uses JavaScript, and can be used on computers that run Windows, Mac OS X, and Linux.
Over 2,900 types of ransomware have been reported, and they’re growing. Here are just a few:
Bad Rabbit
Bad Rabbit has infected organizations in Russia and Eastern Europe and is spreading throughout the world. It does this via a fake Adobe Flash update on compromised websites. When the ransomware infects a machine, users are directed to a payment page demanding .05 bitcoin (about $285).
Cerber
This ransomware encrypts your files using AES encryption and demands a ransom of 1.24 bitcoins (worth $500). It communicates via a text-to-speech voice message, a recording, a web page, or a plain text document. There’s no way to decrypt files that are encrypted by Cerber unless you pay the ransom.
Cryptolocker
CryptoLocker infects computers that run Microsoft Windows. Like other forms of ransomware, you must pay the hackers to decrypt and recover your files. CryptoLocker spreads via fake emails (phishing) designed to mimic legitimate businesses.
CryptoWall
This form of ransomware has been around since 2014, but new variants are still circulating, including CryptoBit, CryptoDefense, CryptoWall 2.0, and CryptoWall 3.0. Like CryptoLocker, CryptoWall is distributed by spam or exploit kits.
CryptXXX
CryptXXX used additional capabilities including network-share encryption. This means that even if you can decrypt your files, it can still cause significant downtime by encrypting files on your network shares.
FakeBsod
FakeBsod uses a malicious piece of JavaScript code to lock your web browser. It displays a fake warning message and tells you to go to a particular webpage (that contains the ransomware). The message says to “contact Microsoft technicians” about an “Error 333 Registry Failure of the operating system – Host: Blue screen Error 0x0000000CE.” When you call the phone number, you’ll be asked to pay a fee to fix the problem.
Lockscreen
This form of ransomware isn’t new and has been in use for quite a while. It attacks Android devices. However, now there’s a new version that is more powerful and much more resilient. It used to lock your screen using a hardcoded passcode, but with the right code, you could unlock your device. Today the new version is impossible to reverse-engineer the passcode since it uses pseudorandom passcodes. Because of this, you can’t unlock your device and must pay the ransom.
Locky
If your computers are infected by Locky, it will rename all of your important files and prevent you from opening them. It does this through encryption and using the file extension–locky. Now, only the cybercriminals have the decryption key, and you must purchase it from them to retrieve your files. To do this, you have to go to the Dark Web and pay $400+ in Bitcoin.
NotPetya
This is a strain of Petya and was first seen in 2016. Today, experts believe NotPetya’s sole purpose is to destroy data instead of obtaining a ransom.
Petya
Petya is especially dangerous because it encrypts entire computer systems, and overwrites the master boot record, so you can’t reboot your operating system.
Spider
Spreads via spam emails. It’s hidden in Microsoft Word documents and installs the ransomware on a computer when it’s downloaded. The Word document (typically disguised as a debt-collection notice) executes macros that encrypt your data.
TeslaCrypta
This uses an AES algorithm to encrypt files and is specifically designed to attack Adobe software vulnerabilities. TeslaCrypta installs itself in the Microsoft temp folder.
TorrentLocker
TorrentLocker spreads via spam email campaigns and targets specific geographic regions. It also uses the AES algorithm to encrypt files. It collects email addresses from your address book to spread malware to your business contacts, friends and family members.
WannaCry
WannaCry has hit over 125,000 organizations in over 150 countries. It currently affects Windows machines through a Microsoft exploit known as EternalBlue.
WannaCrypt
This computer attack began locking down data on May 12, 2017. It affects Microsoft Windows Operating systems. WannaCrypt encrypts all the data in on your computer and holds it hostage.
ZCryptor
This form of ransomware uses a worm-like tactic to self-propagate and encrypt files and external drives so that it can attack other computers.
Part 3
How Ransomware Infects Your Computers
Ransomware attacks are increasing, and so are the ransoms to recover your data.
You’ll know when ransomware infects your computer because the hackers display a message telling you how much to pay to unlock your files. These ransoms typically run in the $300-$500 range. But, some businesses are having to pay upwards of $1,000 per computer. If you have 25 computers that are infected, that’s $25,000.
Hackers primarily use the following attack vectors to infect computers:
Phishing Emails
This is the most common scenario. A realistic-looking email is sent to you with a link or attachment that contains the ransomware. Hackers will often send a number of these links or attachments to hide the one with the malware. Once it’s clicked the malicious software loads itself and the ransomware infection spreads throughout your files, locking them until you pay the ransom.
Drive-by-Downloads
If you unknowingly visit a realistic-looking website containing ransomware, it can load itself onto your computer. If you use an old browser, out-of-date software, or third-party applications, you’ll be most vulnerable. A hacker can detect a vulnerability and exploit it. When a software vendor discovers this, they’ll release a patch to repair the issue, but by this time the criminal has already done their dirty work. Examples include unpatched versions of Adobe Flash, a bug in Java or an old web browser, or an unpatched operating system.
Free Software
A lot of us download free versions of software. Some are legitimate, but others contain ransomware. They are especially prominent in broken versions of expensive games, free games, porn content, screensavers or bogus software. By convincing the user that they should download the software, they can get past firewalls and email filters. You might not even know that you’ve done this until the ransomware activates weeks later.
Unpatched Software
According to the U.S. Computer Readiness Team (CERT) using unpatched and unsupported software may increase the risk of proliferation of cybersecurity threats, such as ransomware. Microsoft provides a guide to help you keep your software up to date. They recommend that you use feed update functionality to stay informed about new ransomware variants and what you should do to protect your data.
Part 4
What to Do If Your Files Get Encrypted.
Tell your employees to let you know if they experience the following:
- They can’t open their files, or they get error messages saying a file is corrupted or contains the wrong extension.
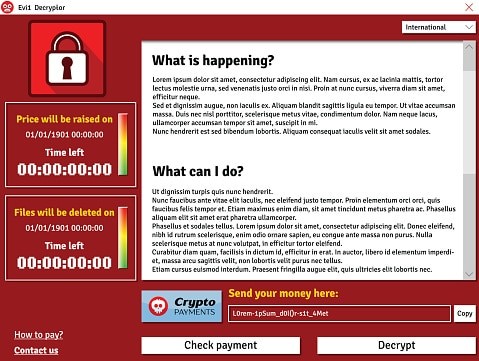
- A window pops up with a ransomware program that they can’t close. This window may contain a message about paying a ransom to unlock files.
- A message says that a countdown has started for a ransom to decrypt files and that it will increase over time.
- They see files in all directories with names like “How to decrypt files.txt or decreypt_instructions.html.”
Ransomware isn’t easy to find while it’s at work encrypting your files. So, you might not know that it’s happening until the hacker sends you a message. By this time, the infection has completed its job. The best thing you can do at this point is to contain the virus from spreading throughout your network.
Unplug the infected computer from your network. You may also need to turn off all network access for all your computers until you know the virus is contained. Set your Basic Input Output System (BIOS) time back if the ransomware has started a countdown. This will hopefully give you more time to recover your critical files and try to eliminate the malware. You can access your BIOS time through the BIOS Setup Utility on the computer.
Restore your files from your last backup. This is why it’s important to regularly backup your files to a safe, offsite cloud location. Just make sure your most recent backup wasn’t infected as well. If you use a Disaster Recovery as a Service (DRaaS) solution, you should be able to do this and quickly “spin up” the DR image on your computer. By spinning up the image in a self-contained virtual machine (VM), you can inspect the DR image without exposing it to your entire network.
Alert the FBI. Don’t pay the ransom. This is a mistake because you still may not get your files back and the criminal will continue to extort you for money.
Unfortunately, recovery from ransomware can be difficult as cybercriminals fine-tune their tactics and become more sophisticated.
Part 5
How to Protect Your Data From Ransomware
ood news is that there are best practices you can adopt to protect your business. The Small Business Administration has these 14 recommendations. Your Technology Solutions Provider can help you with these.
- Implement an awareness and training program. Because end users are targets, employees should be aware of the threat of ransomware and how it is delivered.
- Enable strong spam filters to prevent phishing emails (an attempt to obtain sensitive information electronically) from reaching employees and authenticate inbound email using technologies like Sender Policy Framework (SPF), Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM) to prevent email spoofing.
- Scan all incoming and outgoing emails to detect threats and filter executable files (used to perform computer functions) from reaching employees.
- Configure firewalls to block access to known malicious IP addresses.
- Patch operating systems, software, and firmware on devices. Consider using a centralized patch management system.
- Set anti-virus and anti-malware programs to conduct regular scans automatically.
- Manage the use of privileged accounts based on the principle of least privilege: no employees should be assigned administrative access unless absolutely needed and those with a need for administrator accounts should only use them when necessary.
- Configure access controls—including file, directory, and network share permissions— with least privilege in mind. If an employee only needs to read specific files, the employee should not have write access to those files, directories, or shares.
- Disable macro scripts (toolbar buttons and keyboard shortcut) from office files transmitted via email. Consider using Office Viewer software to open Microsoft Office files transmitted via email instead of full office suite applications.
- Implement Software Restriction Policies (SRP)s or other controls to prevent programs from executing from common ransomware locations, such as temporary folders supporting popular Internet browsers or compression/decompression programs including the AppData/LocalAppData folder.
- Consider disabling Remote Desktop Protocol (RDP) if it is not being used.
- Use application whitelisting, which only allows systems to execute programs known and permitted by security policies.
- Execute operating system environments or specific programs in a virtualized environment.
- Categorize data based on organizational value and implement physical and logical separation of networks and data for different organizational units.
In Conclusion
The increased incidence and rapid evolution of ransomware have raised concerns and stakes for both small and large businesses. Of everything we’ve discussed here, the two most important things to do to protect your business is to use a solid enterprise-grade cloud backup solution and to provide professional Cybersecurity Awareness Training for your employees. In both cases, your Technology Solutions Provider is your best friend. They’ll help you fight and prevent ransomware and cybercrime of all kinds. Don’t wait. Contact them today.